Small Business, Big Lake – Avoiding Common Phishing Scams
When you think phishing, you may think of a nice day on the lake or that 90s band that’s still on tour.
Phishing is not actually the practice of following a certain jam-band religiously, but rather is a more iniquitous topic. Phishing can be defined as an online scammers attempt to gather information from you to be used nefariously by tricking you into thinking they’re someone or a service you’re comfortable sharing your personal information with. Most of us have gotten phishing emails before, but these scammers attempts don’t stop at the inbox.
I get a decent amount of emails wanting to know whether a message from a seemingly-trustworthy source is legitimate. These messages from clients range from supposed Google employees to the traditional Nigerian Prince, and almost none of them are bona fide. Some contain links or documents that direct you to a malicious data-collection site, some rely on the willfulness of the user to forfeit information. With the scam season in full session, I figured it would be appropriate to touch on a few of these scams, how to detect them, and what to do in response.
Advanced-Fee Phishing
The most common form of phishing is done via your inbox, and can be rather primitive compared to some other techniques. Advanced-Fee Phishing, also known as 419 Phishing, involves someone reaching out to you claiming that they need something, that you’ve won something, that you’ve been accepted into a job position, that your bank needs you to take action, or something similarly innocuous. This could be the classic Nigerian Prince (even though Nigeria is not a Monarchy), a suitor looking to win your hand, or an employer interested in hiring you, to name a few examples.
If it’s not strange enough that these people are emailing you out of nowhere, these emails are usually in broken English and are asking for very personal details such as bank information or social security numbers. You shouldn’t feel like a bad person if you don’t help that widow obtain her life-insurance check.
Scare Tactics
A client of ours recently got an email from a supposed “member of an international hacker group” that claimed to already have access to an email account and as proof, supplied the account’s password. The password was in fact the correct one for the account, and our client was understandably freaked out! The message swore that if our client did not send money to a private bitcoin wallet, that the hacker would release our client’s embarrassing private emails and search history. If this seems like something straight out of Black Mirror, that’s because it probably is. If the hacker actually broke in to your account, there would be much more damage.
Spear Phishing
How did the scam artist get that personal account password, you may be wondering? These targeted phishing attempts are getting better and better because data breaches are so common. Internet security is hardly existent, and any information you submit online can and will be stolen and sold. Say you sign up for a free newsletter using the same account information as your Gmail. If this is stolen, someone now has your login information for your email that they can then sell or use for other purposes. Authors of these “scare letters” are either the hackers themselves or the persons who bought the information on the black market.
Spear Phishing is a technique by which the scammer uses information to better pinpoint and personalize their target for greater accuracy. This may not just be your first and last name, but also position at work, cell phone number, or even personal passwords are leveraged to trick or frighten you into giving the phisher money, more information, or company secrets.
“Whaling”
Scammers don’t only target individuals with their schemes. Larger companies are also in the cross-hairs, owing to their organizational structure. Whaling is the practice of Spear Phishing but applied to executives within a business. These can be spoofed intra-office messages or emails from a business partner. Whaling is particularly harmful because it can be used to collect tax information and W2s of employees, harming more than just the targeted executive.
CEOs and other executives are often the targets of Vishing scams as well, where the scammer uses a Voiceover IP server to spoof a legitimate call from a financial institution or business partner and then obtains private company information. This is also known as SMShing if done over text message.
How to respond
The first piece of advice I give clients when asking if a message is a scam is to sit and think about the message for a moment. Why is my bank emailing me instead of calling me? Could this actually be from my bank? What are the details they’re using in the message, and did I give those details out elsewhere?
Most institutions will not contact you via email about most of the scare-tactics that scammers use. Your account will not be shut down if you do not take action, no legal action will be filed against you over email, and you will not be arrested for failing to respond to an email. That’s just ludicrous, albeit scary. Scary enough to get you to click on that link, open that document, or respond with haste.
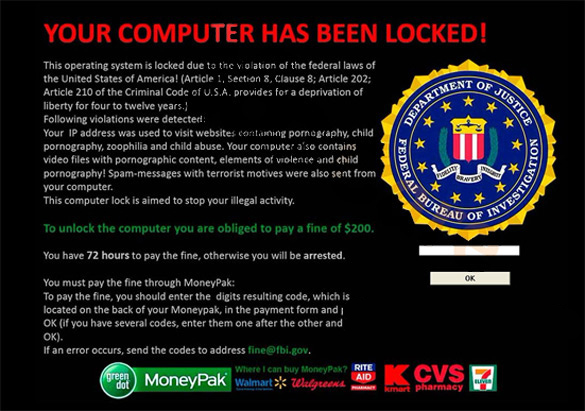
If a link, document, or email is directing you to an insecure site (HTTP), it is possible that it is an attempt to steal information. An SSL certificate (HTTPS) means that all data sent to and from a site is encrypted. Directing users to malicious sites via a hijacked DNS is called Pharming. Mouse over a link to see the linked URL displayed on your machine before you click on anything from within an email. If we are being really careful, I’d suggest reading your email in HTML format to avoid any unwanted redirection.
How can scams be avoided?
They can’t, really. Scammers are just as motivated to get you as cyber-security experts are at keeping you safe. It’s an ever changing issue, and the only thing you can really do to protect against scammers is to pause and be analytical. If something seems phishy, give it a closer look or throw it away.
got a project?
Whether you need a new website or some help with your social media we are ready to start the conversation.

Beginner’s Guide to Dimensions and Metrics in Google Analytics
Beginner's Guide to Dimensions and Metrics in Google Analytics by Isaac Wielhouwer | Jul 17, 2024...
Chatbot Basics 101
Favorite Social Media
What is your favorite social media platform? Remember the days when there was just Myspace? Oh,...
Call to Action Do’s and Don’ts
There is such a thing as a bad call to action The goal of any page on a website, whether it's the...
